Background
Here's what it looks like; I get an e-mail from "Nathan" at computerbright.com explaining that his company owns the .NET version of my domain. Obviously, if I care about branding, I'll want to buy the domain from them. Since benevolence is a pillar of their core beliefs, computerbright.com is willing to part with the domain for a mere $599 dollars. Nathan's mastery of the English language isn't great, which helps raise the first flags of concern on my end, but this doesn't immediately preclude him from actually owning the .NET domain: as far as I know, you can buy a .NET domain from anywhere in the world. Here's Nathan's eloquent pitch to me:
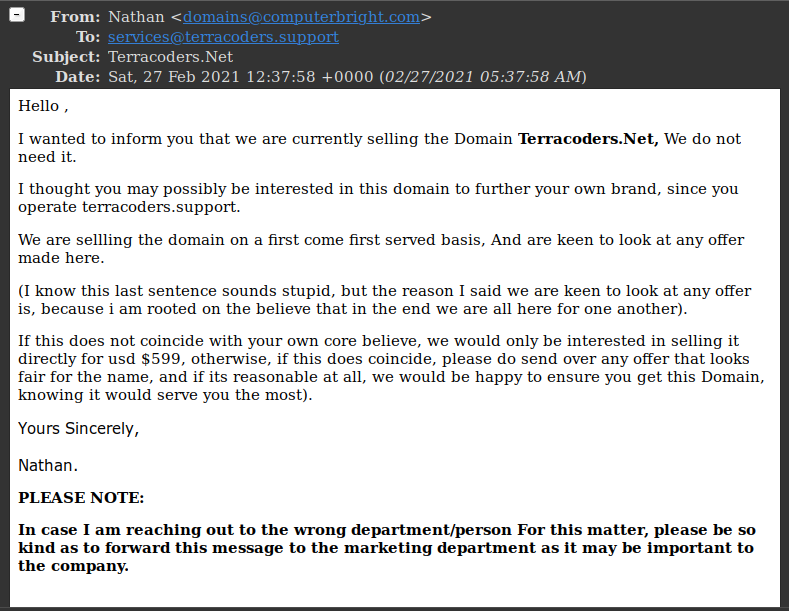
Zero Cares to Give?
In my case, I wouldn't really care one way or another who owns the .NET version of my domain; I'm a freelance developer, not a corporate entity. I do, however, have clients for whom this kind of e-mail would stir panic. At one point, one of my clients had literally dozens of .COM and .ORG domains with a whole mess of redirects to ensure that their brand was safe on the web. These kinds of companies wouldn't bat an eye at $599 dollars for a domain they deemed necessary. All it would take is for some happy-go-lucky-"I've got a wicked Instagram account so I know all about the internet"-marketing-department-go-getter to read this and go: "yeah!... we should buy up the domain from these guys!" They might even feel accomplished for having staved off some sort of fiasco...
The Scam
... except, [enter Admiral Ackbar, stage left] it's a TRAP.
Nathan has made a few shallow, but not entirely implausible, assumptions: one, that his reader doesn't really know how to buy a domain; two, that his reader doesn't know the value of the domain; and, three, that they don't know how to verify ownership of a domain.
If you don't know how to buy a domain, the only remedy is education. However, the second two vulnerabilities can easily be remedied with a quick WHOIS lookup. See, when you buy a domain, it gets registered with a Public Domain Registry. This means that vital info attached to the domain becomes public-facing: the name of the owner, the owner's e-mail address, phone, physical address, etc. As a fascinating side note, it's often this same public facing data that scammers like Nathan use to obtain your e-mail address. Here's the existing WHOIS data for terracoders.support; if terracoders.NET is registered (i.e., belongs) to anyone else, we can expect to see something like this attached to it:
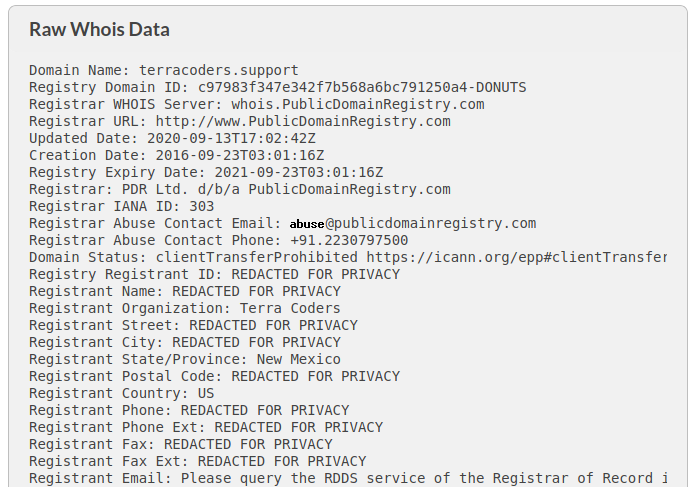
If you weren't aware that this information is public facing, you may wish to enroll in domain privacy with your domain host. This is usually sold at an extra premium (something like an extra $10 a year, per domain, depending on host). This can help prevent people like Nathan from finding your contact info in the first place. If, however, you list your contact info on your website, there's really no hiding from these guys.
Anyhow, let's do a quick WHOIS search for terracoders.NET and see what kind of data we find:
The suspense is killing me!
And... here's what we get:
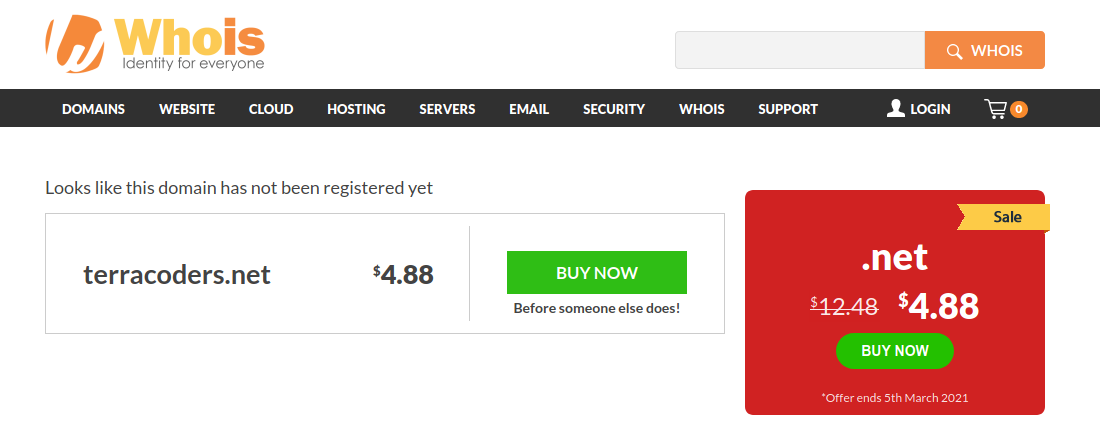
There you have it: the domain has not been registered. Nobody owns it. How the f#$% is it computerbright.com's to sell, then?
Who is Computerbright.com?
No--literally--who do these people think they are?
They don't even own terracoders.NET, but they have the balls to put it up for a $599 ransom when it's advertised on whois.com for a measly $4.88. It's a scam, plain and simple. But, wait!--there's more! [Enter Indiana Jones, stage right]:
Nazis. I hate these guys!
An Alt-Right Connection!?
Out of curiosity, let's see what kind of public-facing info we can gather on computerbright.com. Since they look to offer purchase of domains (namely, their own) from their own site, I would certainly hope that they have a good SSL Certificate. Let's have a look at their certificate real quick:
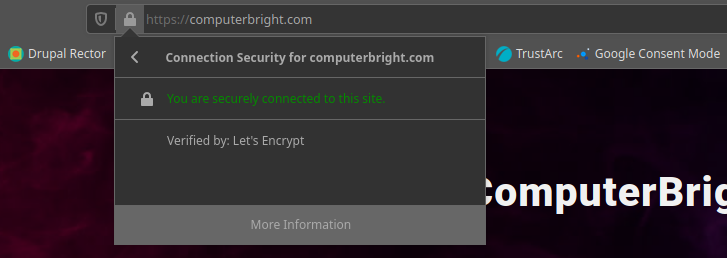
Since I use Let's Encrypt for terracoders.com, and since I've had occasion to deal with multiple other vendors in the industry, I can say in full disclosure, I couldn't recommend Let's Encrypt to a corporate client. I'm not saying you can't or shouldn't necessarily trust sites with Let's Encrypt certificates; again, I use one for this blog. Let me put it another way: Let's Encrypt is to SSL as go-karts are to the freeway. They'll get you where you need to go, but there are better options out there. Personally, their certificate doesn't instill confidence (particularly when attached to a shady domain). When I look at the other domains on the certificate, I can see that each one directs to a site which is essentially a clone of computerbright.com:
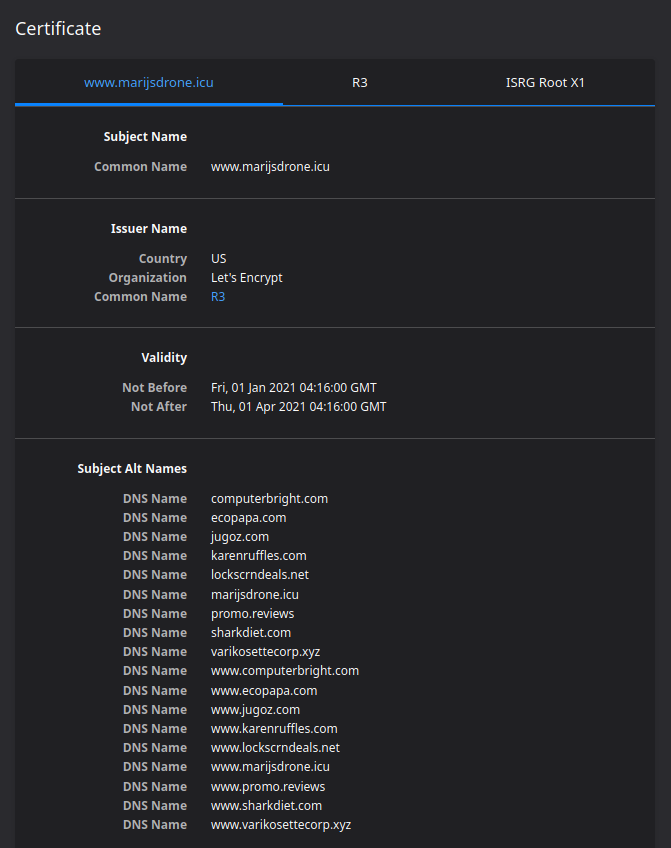
The phrase "Domain Farming" comes to mind. It's like someone is buying up a bunch of random domains on the off-chance they'd be able to monetize them--no matter how obscure. According to this article from Epik blogger, Mr. "Rob Monster", domain farming is a real thing--and, a simple process:
Farming of cash crops is not all that different than raising young domains. If you think about it, Acquire, Develop, Operate, Sell is a near cousin of the farming equivalent of Prepare, Plant, Fertilize and Harvest. This is a gross oversimplification of farming but there is a method to growing things with scale, and that includes websites. As with farming, it can be learned. However, most domainers are still merchants — they can buy and sell, but most have little interest in cultivating.
Now, Epik is a domain registrar and web hosting company. They should know a thing or two about domains. I find it absolutely fascinating that "Mr. Monster" here has taken the focus to cultivation. It's not enough just to buy and sell domains; you also need to fertilize them--to grow their potential for profit. That obviously means rolling up the sleeves for some good old fashioned hard work.
I wonder what that entails...?
I digress. Forgive me.
Let's have a quick look at the WHOIS data for computerbright.com:
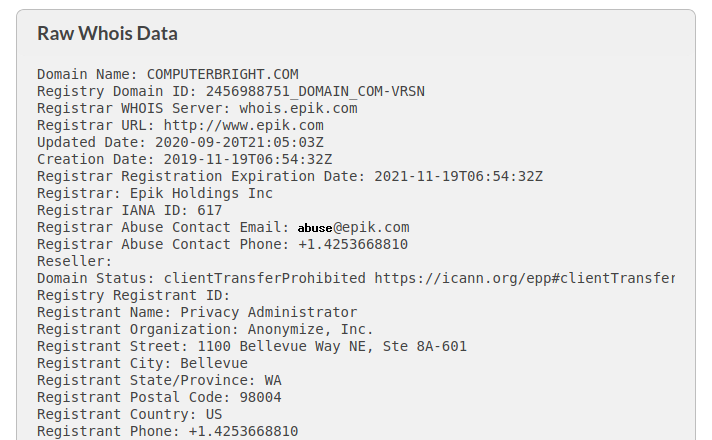
Good god! What a coincidence!?! Computerbright.com was registered with Epik! Imagine that! In fact, the only logo on the computerbright.com website is the Epik logo! The registrant name, Anonymize, Inc., is a company owned by Epik! It's almost like... ... they own the site!? Either way, it's good to see some kids from the old hood carving out a proper living on the net (my old man had a house just down the road from Bellevue; I miss the 425).
Epik may not actually own the site and domain; it's more likely they're acting as a host. Their logo appears alongside a standardized design on all of the domains attached to the aforementioned SSL certificate. It's more likely that they're hosting a platform that allows users to buy up domains and then install a "one button" site on each domain: it comes out-of-the-box ready to channel sales of the domain back to Epik and domain stakeholders.
I wonder if "cultivation" of domains includes ransom?
I've worked with my fair share of domain registrars as well as hosting companies. To be honest, I really know nothing about Epik, beyond the fact that they seem to promote domain whoring. Might as well jump on to DuckDuckGo and see what they're about:

Summary
Some dude contacts me to offer me a domain he doesn't own for $599 dollars. His e-mail is from a domain registered with a company known for providing services to skin head pricks who can't get hosted anywhere else (Parlor, 8chan, 8kun, Rush Limbaugh), their logo featuring prominently on his website. Apparently, this company also believes that whoring and ransoming domains is a business model for the future--cultivation. Whoop-ti-do!!! I can't say whether Epik is directly responsible for the e-mail. Still, you might want to stay away from them. There's definitely some shady stuff going on with their domains and hosting.