Background
One of my first Linux installs was Xubuntu on a 2008 MacPro (at two 3Ghz processors with 4 cores each, 15.6 Gb RAM, and an upgraded GeForce GTX card, it's still a contender in 2020). I bought the computer, prior to upgrade, for about $350 on eBay as a pet project, hoping it could take the place of my 2012 Mac Mini--a computer Apple was no longer looking to support with OS releases. The idea was to install Xubuntu on the MacPro and let one of Apple's last decent computers shine anew. At the time, it seemed like a pain to get Xubuntu to play nice with Apple's hardware. I installed reFind and discovered the joy of getting the OS to play nice with Broadcom Wi-Fi cards.
Suffice it to say, I had no clue what I was doing. After an upgrade to the Linux kernel left my computer with a somewhat fatal bug, and not willing to put in the time to fix it. I recently opted to partition the hard drive and and install Ubuntu alongside Xubuntu. I'd prefer another Xubuntu install, but Ubuntu is what I have on my USB flash... so, that's what we use...
If I can just get Ubuntu running, I can go in and at the very least recover my files...
A quick Ubuntu install later, I hit the file browser and find my way to my user directory on the Xubuntu partition:
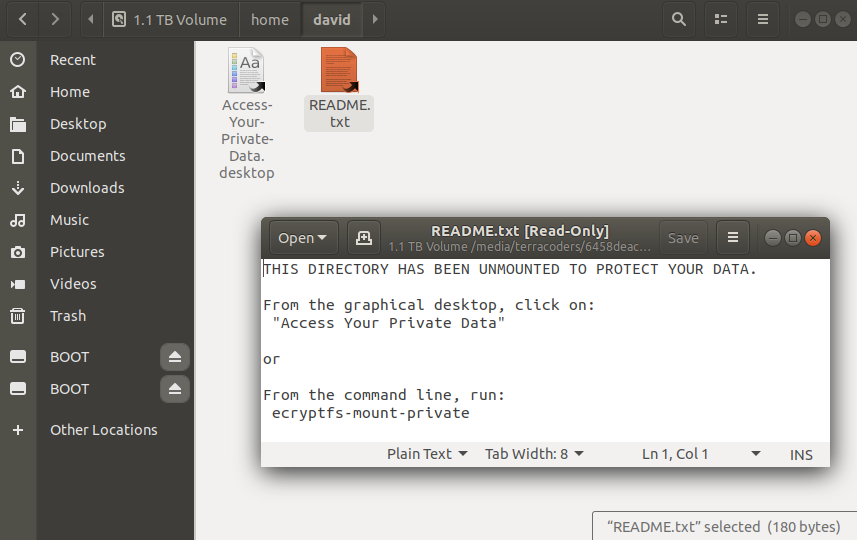
Welp... that's not gonna work. There's not a lot of context in that README.txt, but I gather that the directory is encrypted and I should probably hit the command-line. I open the Terminal, run encryptfs-mount-private and get some not entirely unexpected business about the command not being found. After some quick Google-Fu, I see that I'll need to install this functionality with sudo apt-get install ecryptfs-utils. At this point, I still don't even recall setting the directory up as encrypted, so this is all still rather mystifying.
Wasting Time with a Manual Decryption
Pro Tip: don't.
The documentation for how to recover encrypted data manually looks thorough; you may be tempted to wander down this path. There's just enough ambiguity there, though, to lead you down a rabbit hole of failure. The automatic method is much easier, although it comes with it's own challenges.
Automatic Decryption
Success here relies on a couple of things:
- You remember the login password that's tied to the files you're trying to access
- You understand where your encrypted files are actually kept
Let's take a quick look at what the documentation says about Automatic Decryption:
- boot the target system using an Ubuntu 11.04 Desktop LiveCD
- make sure that your target system's hard drive is mounted
- open a terminal
- run 'sudo ecryptfs-recover-private'
- follow the prompts
- access your decrypted data and save somewhere else
Can it be that easy?--no.
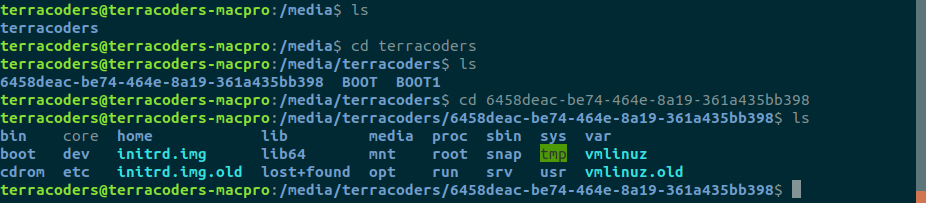
But, let's play along either way. First thing's first: you'll need to have whatever partition your enrcypted folder/files are on mounted; I did this from the desktop. You'll also want to be able to find those folders/files via the command line. You should be able to find the partition under the /media/user folder once you've got it mounted. Here's an example from my own terminal:
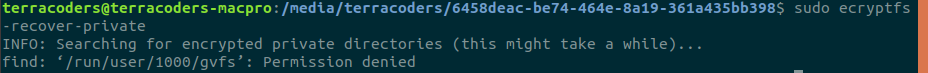
Of course, the next step is logically to run sudo ecryptfs-recover-private
What happens if we do that? Not a whole lot. See, according to the manpage, unless you specifically tell ecryptfs-recover-private which folder you'd like decrypted, it will try and find encrypted directories on it's own--and it doesn't seem to look for them on partitions beyond the partition you're booting from. If you run it without specifying a directory, you're likely to see this:
So the trick then is to tell the function where to look.
Naturally, you'd think that since this all began in the /home/user folder (remember--that's where I found the README.txt explaining that the folder was encrypted), that would be the directory we specify. You'd be utterly wrong, though. Here is where you'll need to do some digging. On the command line, you should be able to find your encrypted files, and they won't be in /home/user; rather, you'll need to find the following directory /home/.ecryptfs/user/.Private; if you run ls in that directory you should see all your encrypted files--like this:
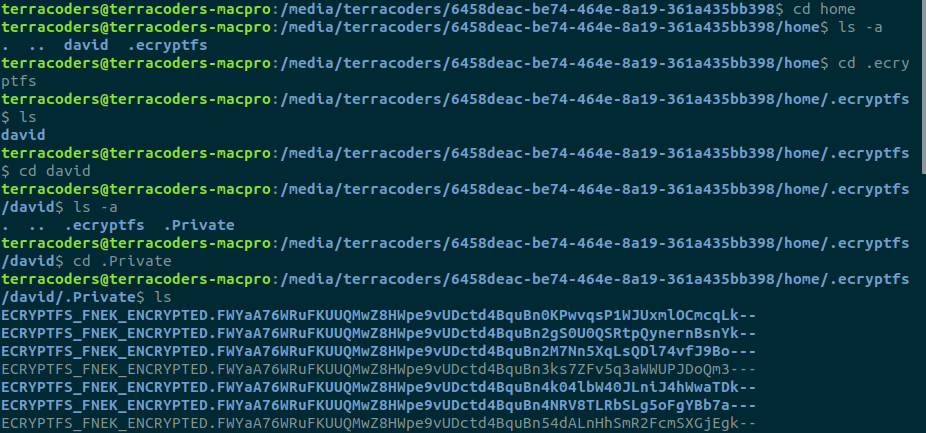
So, with that, we now know how to run the command--it should look like this:
$ sudo ecryptfs-recover-private /media/host_user/disk_identifier/home/.ecryptfs/target_user/.Private
Here, "host_user" is of course the user name for your boot OS login; "target_user" is the username to whom the encrypted files belong on the partition you're trying to recover.
You should see an output like this:
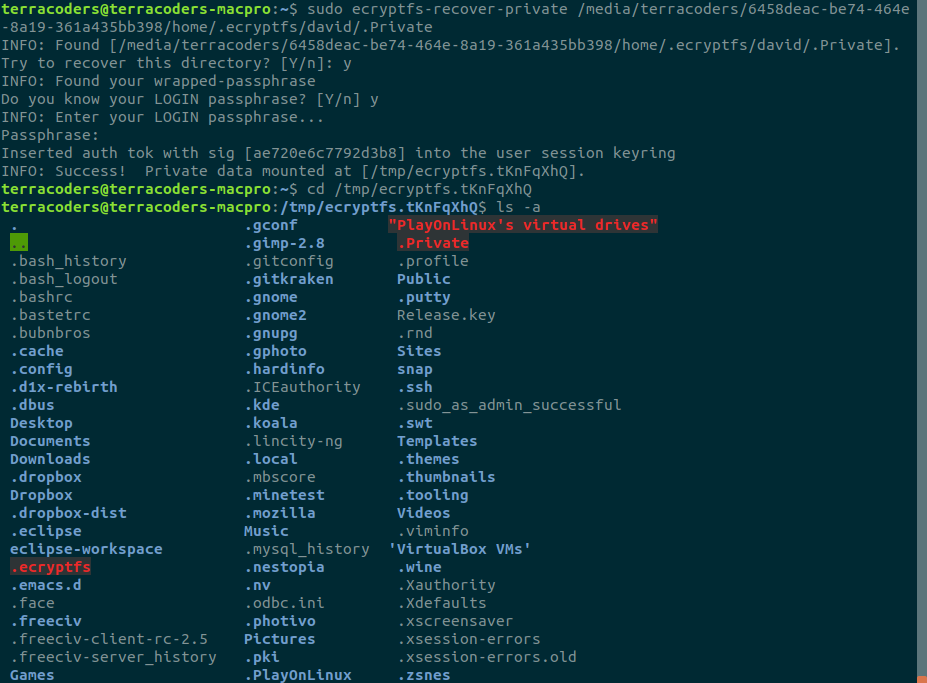
And, that should be that! Your decrypted files should now be accessible from the folder specified in the output: