Think it's only executables (i.e., .exe files) you need to stay away from? Think again. Today, that virus is coming to you courtesy of your good friend: the MS Word document. But first, let's look at the delivery. Today's attack comes with a bittersweet coating of Social Engineering.
Common Vectors of Attack: Social Engineering
What exactly is "Social Engineering"? In simple terms: it's a story--a story woven with the sole purpose of getting you to lower your guard. Most of us don't just open our doors to anyone who knocks; we need a good reason--a sense of urgency or trust. Web-savvy evildoers are well aware of this, and it's intriguing to see what kinds of characters they dream up to foster urgency and trust. Sometimes the stories are just too good to believe: "I, the prince of Nigeria, need you to hold on to my millions of dollars for a bit." The story I got fed today, however, has a level of "emotional" sophistication I don't think I've normally seen.
Today's attack comes from one "Catalina Perez". Catalina here is most likely the owner of a hacked Hotmail account. She's also contacted me in Spanish. Being half Colombian, I actually do fend for myself en el idioma de mi padre. I don't go out of my way to use the language these days, but I have acquaintances old and new who speak Spanish. Living in New Mexico, I also have plenty of neighbors who speak Spanish: it wouldn't be all that out of place for me to receive an e-mail in Spanish. That's not a big trigger for me.
So let's have a look at Catalina's message; I hope you remember your high school Spanish. I'll give a loose translation below for those who don't get it:
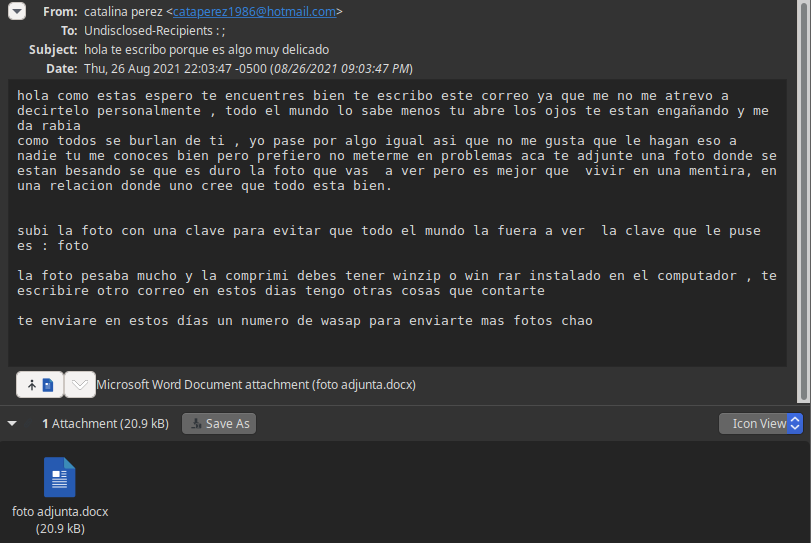
It reads more or less like this:
Hi, how are you? I hope well. I'm writing you because I'd never dare to approach you in person. Everybody knows it but you. Open your eyes... blah blah... I can't stand that everyone is laughing at you because the same thing happened to me... blah blah... you know me well, but I don't want to get caught up in this. I've attached a photo of the two of them kissing. I know it's hard to see, but it's better than living in a relationship where you believe everything is alright.
I put a password on the photo so that the whole world doesn't see it. The password is: photo
The photo was really big, so I compressed it. You'll need WinZip or WinRAR installed on your computer. Blah blah...
I'll send you a WhatsApp number soon so that I can send you more photos.
There you have it! Mystery! Intrigue! Could it possibly be so? Is my wife cheating on me? Imagine: you're having trouble in your relationship and you get an e-mail like this. The lack of a signature, the vagueness of the message, it's all part of the story: "I'm someone close to you; think of me as your guardian angel; I don't want to get caught up in it all, but I'm here to tell you the truth; I'm here to help you: open this file!!--(and be sure to have WinZip or WinRAR installed)". What a tech-savvy little guardian angel we have!--password protecting files and compressing data!!
These are, of course, dead giveaways: the attached Word document isn't compressed. You can see that as plain as day. Sadly, being on Linux, I won't be downloading WinZip or WinRAR, either.
But, what's this really about? What's the actual attack here? Somebody sent me a MS Word document; how dangerous can those actually be? Being on Linux, I was actually tempted to open this file and see if I could figure it out--maybe drop it into a VM and fire up LibreOffice. "Meh... but that'll take way too long... let's do a quick search on DuckDuckGo:"
One of the first hits: How to Create and Obfuscate a Virus Inside a Microsoft Word Document
That's actually an article from 5 years ago. So, Catalina's attack probably isn't the exact same one documented above. Indeed, as far as I know macros can only be used to payload viruses onto .docm files, and the one attached to my mail is a .docx file. I may still have to get a VM fired up.
Either way, it's more or less obvious what's at stake here.
RansomeWare: It's Definitely RansomeWare!
Catalina, or her ghost writer, has given us more than a few clues as to what she's up to. The attachment isn't an archive (it's not zipped), so why would she/the attacker want us to be sure to have WinZip or WinRAR installed? Because they intend to use it, of course! Whatever can be used to unzip a file can also be used to zip it. I hope you're also aware that .zip and other archive formats can also be password protected. The trick, then, is pretty straight forward: I get you to open a Word document. That word document runs a script that takes, say, everything in your user folder and stuffs it into a password protected zip file. Then it deletes everything in your user folder: bank info, receipts, sensitive information, family photos, etc. Wanna get your info back? Send your attacker a couple thousand in BitCoin and they give you a password.
It's an increasingly popular attack.
So, how do you defend against it?
Playing Defense
Here are a couple of things you can do so that you don't get duped by this:
1). Don't open shit sent from people you don't know; and be skeptical of anything in the grey: people who literally say they know you; people who claim urgency; etc.
2). Turn off Macros in MS Word. Do a quick search on DuckDuckGo if you're not sure how to do it.
3). Back your shit up! On Linux, we have DejaDup/Duplicity--a really nifty tool for managing backups. On Ubuntu this application runs from the App Grid as "Backups"; it should be a default application on most Ubuntu installs. You can specify which directories you'd like to back up, and the backups should be encrypted. Be sure to store your backups on an external hard drive. If you're running a Mac or PC, you should be able to find a similar application. I won't go quite as far as most attackers would and say, "if you get suckered by this, you deserve to get suckered." But if you're not running backups on your most sensitive files, ransomeware aside, you're asking for trouble.
Stay safe, people. Don't get duped by this kind of garbage!